Table of Contents
We’ve all heard about password security fails, but this week’s letter takes the cake. It’s a wild ride through a landscape of truly terrible password practices, and it’s a stark reminder of why small business cybersecurity is so crucial.
Dear Tech Bear,
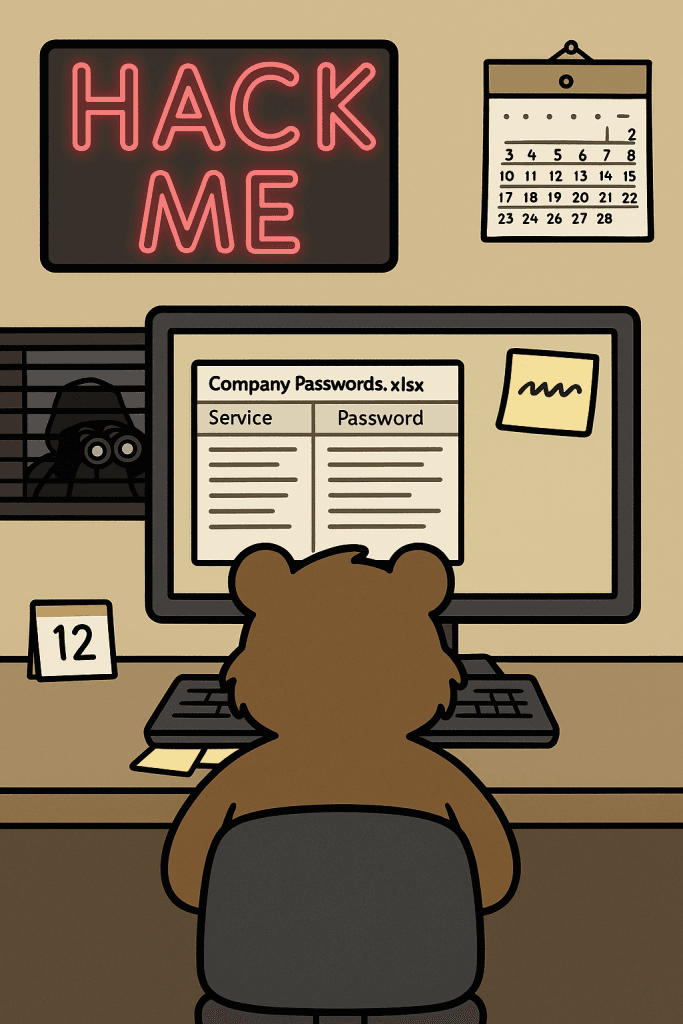
I’ve created the perfect password system, but my former IT guy said these practices are a password security failure. All of our company passwords are “password” followed by the current month number. We change them monthly for security! Plus, I’ve created a shared spreadsheet on my company’s network drive so everyone can see it. It was a hassle having to remember a password to open it, so I just left it in plain text. My IT support guy quit last week for unrelated reasons.
Before the spreadsheet, everyone just wrote their passwords on sticky notes and put them under the keyboard or stuck them on their monitor. I think the spreadsheet is a security improvement.
How impressed should I be with myself?
Security Genius in Sacramento
Oh my sweet summer child…
Your “perfect” password system isn’t security—it’s a welcome mat for hackers with a calendar and a treasure map! And those sticky notes? Might as well put up a billboard with your bank account details, illuminated by a flashing neon sign that reads “Easy Access!” In the digital wilderness of small business cybersecurity, your current strategy isn’t just flawed; it’s a masterclass in how not to protect your sensitive information. This is a case study in password security fails.
Let’s dissect this double dose of digital danger, shall we? We’ll explore the critical importance of password management and the perils of neglecting basic data protection. We’ll also delve into why these seemingly “convenient” solutions are, in fact, a major cybersecurity nightmare.
Act One: The Chronically Insecure “PasswordMonth” Strategy
This first act is a classic example of a password security failure. While the intention of changing passwords monthly might seem like a good security practice, the predictable nature of your system completely negates any potential benefit. Here’s why this approach to password security is flawed:
Trivial Predictability: Attackers are well aware of common password patterns. Adding a sequential number like the month makes it incredibly easy to guess. Once they crack one month’s password, they have a high probability of predicting future (and potentially past) passwords. This severely undermines your cybersecurity efforts and is a prime example of a password security failure.
The problem is that it lacks complexity. A strong password should be a random string of characters, not something that a hacker can easily guess.
The Sticky Note Vulnerability: Writing passwords down, especially in plain sight on sticky notes, is akin to handing the keys to your digital kingdom to anyone who walks by. These notes are easily lost, copied, or photographed, creating a significant security risk. It’s hard to overstate how common, and how dangerous, this password security fail is.
Lack of Uniqueness: Reusing the base password “password” across all services, even with a monthly number, means that if one account is compromised, all of them are vulnerable. This violates a fundamental principle of effective password management: unique passwords for each account. This is a basic rule of password security.
Internal Threat: Disgruntled employees or even cleaning staff could easily gain access to sensitive information with such an insecure system. This highlights the importance of robust internal security protocols. Even with the best intentions, insider threats can exploit weak password security.
The Human Factor: Relying on manual monthly updates is prone to error. Employees might forget to change their passwords, use variations, or simply get lazy, further weakening the already flimsy security. Human error is a major contributor to password security fails.
Act Two: The “Convenient” Plain Text Password Spreadsheet
And now, for the encore of this security circus: the shared spreadsheet of usernames and passwords in plain text. Oh, Sacramento, where do I even begin with this egregious data protection blunder? This takes password security fails to a whole new level.
Unencrypted Exposure: Storing passwords in plain text is like keeping the combination to your safe written on the safe itself. Anyone with access to that network drive (internal or external, if your network isn’t properly secured) can see everything. This is a massive cybersecurity vulnerability. It’s a fundamental misunderstanding of password security.
Single Point of Failure: If that spreadsheet is compromised (through a network breach, a disgruntled employee, or even accidental deletion without proper backups), your entire company’s digital life is exposed. Proper data backup and recovery procedures are essential to mitigate such risks. This spreadsheet creates a single, catastrophic point of failure for your password security.
Audit Trail Nightmare: Who accessed what and when? With a shared, unencrypted spreadsheet, tracking any potential security breaches or unauthorized access becomes virtually impossible. This lack of accountability is a serious security concern. You’d have no way of knowing who accessed this incredibly sensitive data.
Ignoring Basic Security Principles: This practice flies in the face of even the most rudimentary data protection guidelines. It screams “we don’t care about security!” to anyone who might be looking.
The Gymnarctos Approach to Robust Password Management for Small Businesses
Enough with the password security fails! True cybersecurity for small businesses and home users requires a multi-layered approach, starting with secure password management. Let’s talk about how to do password security right.
🔒 Unique, complex passwords for each service: (that aren’t just “password” with sprinkles). These should be a random mix of uppercase and lowercase letters, numbers, and symbols. Aim for a length of at least 12-16 characters. Consider using a strong password generator (like Bitwarden).
🔒 Secure password manager: To store and generate strong credentials, tools like LastPass, 1Password , and Bitwarden offer a way to store your passwords securely, generate strong ones to use elsewhere, and even auto-fill them, eliminating the need for sticky notes and unprotected spreadsheets. These are crucial tools for effective IT support and data protection. We highly recommend exploring these password management solutions. You can also find more information about these tools in our article on small business and home user cybersecurity.
🔒 Multi-factor authentication (MFA): Use multi-factor authentication wherever possible. This adds an extra layer of security by requiring a second verification method, such as a code from an app on your phone, in addition to your password. This significantly reduces the risk of someone accessing your account, even if they somehow obtain your password. If you’re not using MFA, you’re leaving yourself vulnerable to a major password security fail. Learn more about implementing MFA and why it’s essential for online safety in our guide to MFA.
🔒 Regular security awareness training: This emphasizes the dangers of weak passwords and unencrypted storage. Educating your team (or yourself) about password best practices, phishing scams, and other cyber threats is crucial for building a strong security culture.
🔒 Securely delete that password spreadsheet immediately and ensure it cannot be recovered. Implement secure file deletion methods to prevent data recovery of the insecure file.
Your IT support guy didn’t quit—he experienced a full-blown existential crisis induced by the sheer ineptitude of your password protocols and the sheer terror of that password spreadsheet. He was last seen muttering about the inherent insecurity of sequential numbering and the horrifying vulnerability of plain text credentials while rocking back and forth in a padded room at the Shady Pines Asylum for the Technologically Traumatized. For comfort and a semblance of control in his new environment, the sympathetic staff has even provided him with a meticulously configured, air-gapped homebrewed Linux server. It’s rumored he’s attempting to achieve technological equilibrium by writing bash scripts that automatically generate truly random and unguessable passwords, a stark contrast to his previous reality. They’ve confiscated all sticky notes and calendars within a five-mile radius of the facility, just in case.
The sheer magnitude of these password fails is… well, it’s a cautionary tale that should be etched in the annals of internet insecurity. Don’t let your small business cybersecurity become a similar cautionary tale.
Next time, please, please, please, leave the password management to the professionals and tools designed for the 21st century. Your data, your business, and any future IT support you manage to hire will be eternally grateful.
About TechBear
Emerging from the deepest, darkest corners of the digital frontier (and occasionally a dumpster behind a tech convention), Tech Bear is the grizzled veteran of countless coding conflicts and the sole reason your toaster oven isn’t currently launching a DDoS attack. Legend has it he single-handedly debugged the Y2K bug using nothing but a rusty keyboard and sheer willpower, and some whisper he accidentally invented the internet during a particularly spirited debate with a sentient toaster. When not dispensing tech wisdom with a healthy dose of ursine sarcasm, he can be found arguing with his smart fridge about the optimal temperature for salmon and training squirrels to perform basic network diagnostics.
#CyberSecurityFails #PasswordManagementMistakes #SmallBusinessSecurity #DataBreachWaitingToHappen #TechHumor #AskTechBear #SecurityAwareness #DigitalSafety #PasswordSpreadsheetFail #StickyNoteSecurity #ITSupportFail #DataProtectionTips #PasswordSecurity
