The Fabulous World of Assistive Technology: Honey, Your Phone Already Knows You Better Than Your Therapist
Ever wonder why some tech just works for everyone? TechBear explains the magic of universal design and how accessibility leads to better experiences for all.
TechBear’s Maintenance Monday: Clean your Tech! Honey, Your Devices are FILTHY!
Sweetie, listen up! Your tech is SCREAMING for attention, and I can practically hear your laptop fans wheezing from here. It’s time for another Maintenance Monday with TechBear, where we’re gonna get all your dusty, crusty devices back to their glamorous selves because it’s high time you clean your tech! The SCANDAL of Your Neglected Tech Lord, have mercy, y’all. I walked into a client’s office last week and nearly blue-screened when I saw what they called a “workstation.” Their laptop was balancing on a stack of old invoices, running hotter than my temper when someone says “have you tried turning it off and on again?” for the fifteenth time in a day. Clearly, nobody had bothered to clean their tech in ages! Let me tell you something, sugar—electronics and heat are like me and unsolicited tech advice: WE DON’T MIX. Your devices are BEGGING for some regular TLC, and today I’m gonna show you how to serve up that computer maintenance realness that’ll keep your tech as smooth and flawless as my highlight when I’ve got a client meeting at 9 and brunch with friends at noon. Laptop Elevation: Give Those Queens Some ALTITUDE! First things first, honey—if your laptop is sitting flat on your desk, table, or heaven forbid, your ACTUAL LAP, we need to have words. Listen here: your laptop needs to BREATHE, and I mean from ALL sides. Those intake vents on the bottom and sides? They’re not decorative! They’re how your computer pulls in cool air to keep all them expensive bits from melting into a puddle of silicon tears. Regular efforts to clean your tech, especially those vents, are crucial! The SCANDAL of Cluttered Desks Let me paint you a picture of what I see in 90% of home offices: Laptop crammed between stacks of paper, coffee mugs, external drives, and enough random cables to recreate the Amazon rainforest. Your poor computer is GASPING for air! Computer maintenance tips start with a clean desk! You need at least 3-4 inches of clearance on ALL sides of your device. That means: DECLUTTER, people! A clean desk isn’t just aesthetically pleasing—it’s essential for your tech’s survival! Lack of airflow is a prime cause of laptop overheating. Now, get yourself a proper laptop stand or cooling pad, sweetheart. Personally, I love those aluminum raised trays that: A good laptop stand costs between $20-50, which is a BARGAIN compared to replacing a motherboard that’s been slow-cooked because you were trying to save desk space. Space-saving doesn’t mean cramming everything together like sardines in a tin! That’s not being efficient; that’s being foolish—and TechBear doesn’t have time for foolishness. ZD Net has a good guide to laptop cooling that has been updated for 2025 Dust-Busting: The ABSOLUTE NIGHTMARE of What’s Inside Your Devices Bless your hearts, if you could see what I’ve seen inside computers that “run a little slow”—the dust bunnies have formed entire civilizations in there! They’re holding elections and building infrastructure! This underscores why regular efforts to clean your tech internally are so important. Dust removal for electronics starts with this holy grail: Canned Air! Here’s what you need in your cleaning arsenal: Canned Air: The Holy Grail Get yourself some compressed air, but listen CAREFULLY to how to use it: Use your canned air to blow dust from: Antistatic Vacuum: For Those Who Mean BUSINESS If you’re running a small business or you’re just serious about your tech (as you SHOULD be), invest in an antistatic vacuum. Regular vacuums generate static electricity that can fry your components faster than my patience frazzles when someone asks me if “the internet is down” when their browser won’t load. A proper antistatic vacuum: They’re pricier than canned air (usually $40-100), but they’re reusable and more thorough. Worth every penny if you ask me, and honey, you ARE asking me—that’s why you’re reading TechBear’s advice column! Screen Cleaning: Stop Using Your T-SHIRT Right Now! If you knew the NUMBER OF TIMES that I’ve watched someone lick their finger and wipe their screen! Sweet Jesus, take the wheel! Now, let’s talk about your screens. To properly clean your tech, you can’t forget these delicate displays! Your screens deserve proper care with: Microfiber Cloths: The ONLY Fabric That Should Touch Your Screen Get yourself a pack of proper microfiber cloths and keep them clean. Wash them separately from your other laundry, with no fabric softener. They should be softer than my heart when a client actually follows my advice. Screen-Safe Cleaners: Because Windex Is for Your House’s Windows, Not WINDOWS OS For the love of all things digital, put down the household cleaners! Your screen is not a bathroom mirror! Invest in a proper electronics-safe screen cleaner that: Apply to your microfiber cloth first—NEVER spray directly on the screen unless you want to see TechBear have a conniption fit. Cell Phone Sanitation: The NASTIEST Thing You Own Y’all take your phones EVERYWHERE, and I do mean everywhere. Studies by the National Institute of Health (like this one)show your phone has more bacteria than a toilet seat, which is just about the most disgusting thing I can imagine, and I’ve seen your son’s browser history. Let me explain why a daily phone cleaning guide should be your new best friend! Clean your phone DAILY with: And for the love of all things holy, take your phone out of its case once a month and clean underneath! The HORRORS I’ve seen when removing phone cases would make a horror movie director faint. Ports and Connectors: The DRAMA of Dirt Your charging ports and headphone jacks are collecting more lint than a dryer filter. When your phone stops charging properly, the first step should be to clean your tech by carefully clearing these ports. Carefully clean ports with: And listen closely because this is CRITICAL: NO METAL IMPLEMENTS EVER! No paperclips, no safety pins, no metal tools of any kind! One tiny slip with a metal object and you’ve just created a short
Ask Tech Bear: Password Security Fails — A Cybersecurity Comedy of Errors
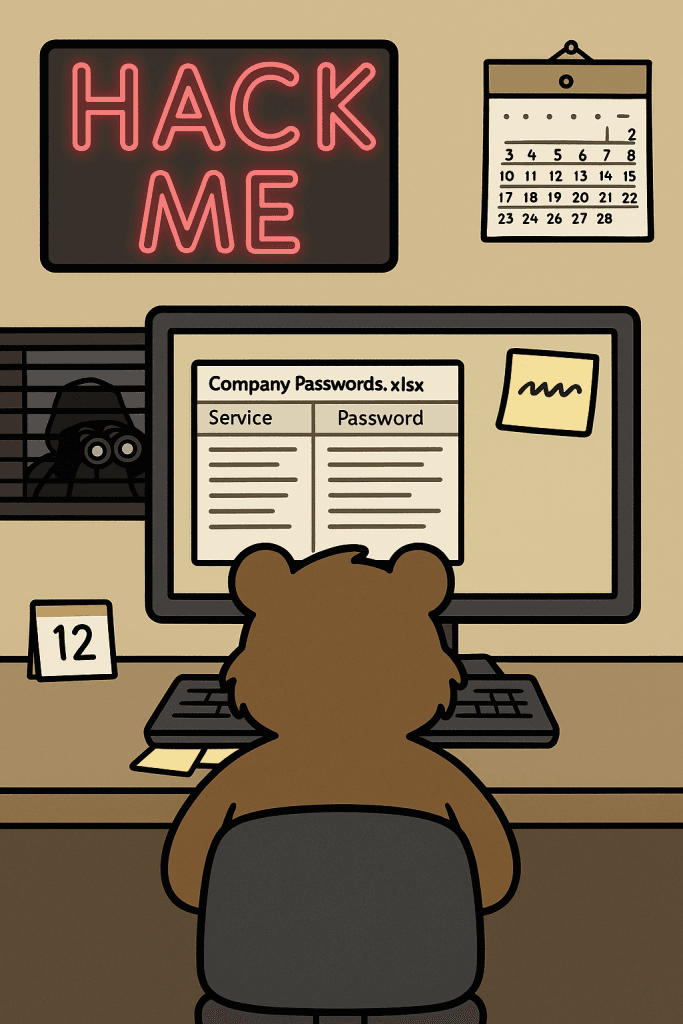
We’ve all heard about password security fails, but this week’s letter takes the cake. It’s a wild ride through a landscape of truly terrible password practices, and it’s a stark reminder of why small business cybersecurity is so crucial. Dear Tech Bear, I’ve created the perfect password system, but my former IT guy said these practices are a password security failure. All of our company passwords are “password” followed by the current month number. We change them monthly for security! Plus, I’ve created a shared spreadsheet on my company’s network drive so everyone can see it. It was a hassle having to remember a password to open it, so I just left it in plain text. My IT support guy quit last week for unrelated reasons. Before the spreadsheet, everyone just wrote their passwords on sticky notes and put them under the keyboard or stuck them on their monitor. I think the spreadsheet is a security improvement. How impressed should I be with myself? Security Genius in Sacramento Oh my sweet summer child… Your “perfect” password system isn’t security—it’s a welcome mat for hackers with a calendar and a treasure map! And those sticky notes? Might as well put up a billboard with your bank account details, illuminated by a flashing neon sign that reads “Easy Access!” In the digital wilderness of small business cybersecurity, your current strategy isn’t just flawed; it’s a masterclass in how not to protect your sensitive information. This is a case study in password security fails. Let’s dissect this double dose of digital danger, shall we? We’ll explore the critical importance of password management and the perils of neglecting basic data protection. We’ll also delve into why these seemingly “convenient” solutions are, in fact, a major cybersecurity nightmare. Act One: The Chronically Insecure “PasswordMonth” Strategy This first act is a classic example of a password security failure. While the intention of changing passwords monthly might seem like a good security practice, the predictable nature of your system completely negates any potential benefit. Here’s why this approach to password security is flawed: Trivial Predictability: Attackers are well aware of common password patterns. Adding a sequential number like the month makes it incredibly easy to guess. Once they crack one month’s password, they have a high probability of predicting future (and potentially past) passwords. This severely undermines your cybersecurity efforts and is a prime example of a password security failure. The problem is that it lacks complexity. A strong password should be a random string of characters, not something that a hacker can easily guess. The Sticky Note Vulnerability: Writing passwords down, especially in plain sight on sticky notes, is akin to handing the keys to your digital kingdom to anyone who walks by. These notes are easily lost, copied, or photographed, creating a significant security risk. It’s hard to overstate how common, and how dangerous, this password security fail is. Lack of Uniqueness: Reusing the base password “password” across all services, even with a monthly number, means that if one account is compromised, all of them are vulnerable. This violates a fundamental principle of effective password management: unique passwords for each account. This is a basic rule of password security. Internal Threat: Disgruntled employees or even cleaning staff could easily gain access to sensitive information with such an insecure system. This highlights the importance of robust internal security protocols. Even with the best intentions, insider threats can exploit weak password security. The Human Factor: Relying on manual monthly updates is prone to error. Employees might forget to change their passwords, use variations, or simply get lazy, further weakening the already flimsy security. Human error is a major contributor to password security fails. Act Two: The “Convenient” Plain Text Password Spreadsheet And now, for the encore of this security circus: the shared spreadsheet of usernames and passwords in plain text. Oh, Sacramento, where do I even begin with this egregious data protection blunder? This takes password security fails to a whole new level. Unencrypted Exposure: Storing passwords in plain text is like keeping the combination to your safe written on the safe itself. Anyone with access to that network drive (internal or external, if your network isn’t properly secured) can see everything. This is a massive cybersecurity vulnerability. It’s a fundamental misunderstanding of password security. Single Point of Failure: If that spreadsheet is compromised (through a network breach, a disgruntled employee, or even accidental deletion without proper backups), your entire company’s digital life is exposed. Proper data backup and recovery procedures are essential to mitigate such risks. This spreadsheet creates a single, catastrophic point of failure for your password security. Audit Trail Nightmare: Who accessed what and when? With a shared, unencrypted spreadsheet, tracking any potential security breaches or unauthorized access becomes virtually impossible. This lack of accountability is a serious security concern. You’d have no way of knowing who accessed this incredibly sensitive data. Ignoring Basic Security Principles: This practice flies in the face of even the most rudimentary data protection guidelines. It screams “we don’t care about security!” to anyone who might be looking. The Gymnarctos Approach to Robust Password Management for Small Businesses Enough with the password security fails! True cybersecurity for small businesses and home users requires a multi-layered approach, starting with secure password management. Let’s talk about how to do password security right. 🔒 Unique, complex passwords for each service: (that aren’t just “password” with sprinkles). These should be a random mix of uppercase and lowercase letters, numbers, and symbols. Aim for a length of at least 12-16 characters. Consider using a strong password generator (like Bitwarden). 🔒 Secure password manager: To store and generate strong credentials, tools like LastPass, 1Password , and Bitwarden offer a way to store your passwords securely, generate strong ones to use elsewhere, and even auto-fill them, eliminating the need for sticky notes and unprotected spreadsheets. These are crucial tools for effective IT support and data protection. We highly recommend exploring these password management solutions. You
