Thoughtful Thursday: The Impact of Data Privacy on Targeted Ads and Your Digital Footprint
Ever wonder why you keep seeing ads for things that have absolutely nothing to do with what you care about? With all the data companies collect about us, you’d think they’d have it figured out by now. In this week’s Thoughtful Thursday, we dive into the world of data privacy, digital footprints, and why, despite the mountains of information they have, your targeted ads might still be completely off the mark.
Ask Tech Bear: Password Security Fails — A Cybersecurity Comedy of Errors
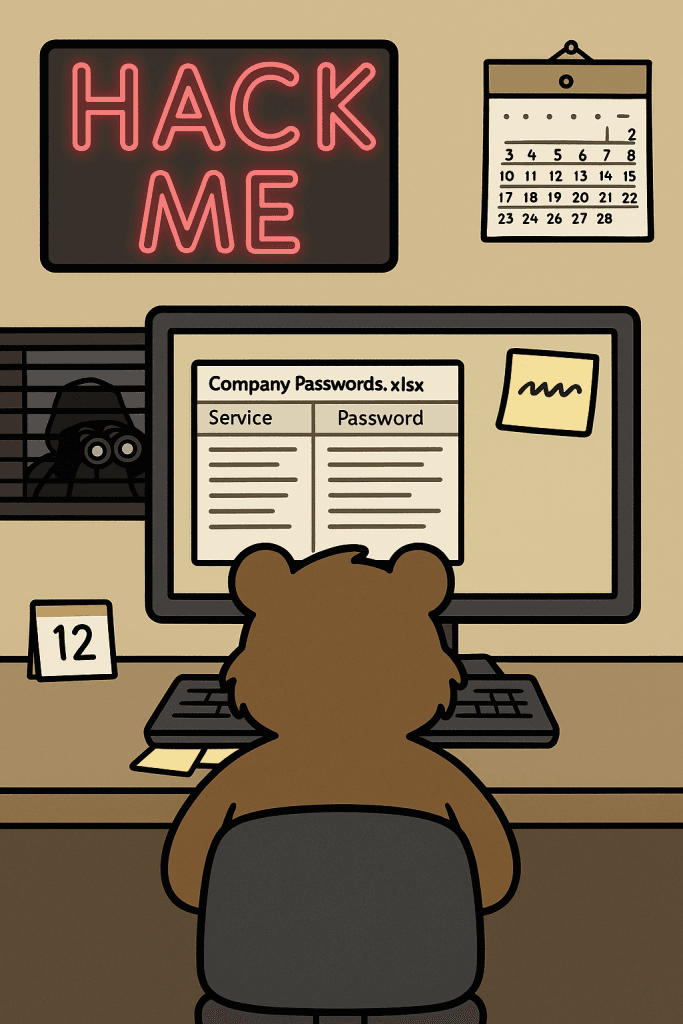
We’ve all heard about password security fails, but this week’s letter takes the cake. It’s a wild ride through a landscape of truly terrible password practices, and it’s a stark reminder of why small business cybersecurity is so crucial. Dear Tech Bear, I’ve created the perfect password system, but my former IT guy said these practices are a password security failure. All of our company passwords are “password” followed by the current month number. We change them monthly for security! Plus, I’ve created a shared spreadsheet on my company’s network drive so everyone can see it. It was a hassle having to remember a password to open it, so I just left it in plain text. My IT support guy quit last week for unrelated reasons. Before the spreadsheet, everyone just wrote their passwords on sticky notes and put them under the keyboard or stuck them on their monitor. I think the spreadsheet is a security improvement. How impressed should I be with myself? Security Genius in Sacramento Oh my sweet summer child… Your “perfect” password system isn’t security—it’s a welcome mat for hackers with a calendar and a treasure map! And those sticky notes? Might as well put up a billboard with your bank account details, illuminated by a flashing neon sign that reads “Easy Access!” In the digital wilderness of small business cybersecurity, your current strategy isn’t just flawed; it’s a masterclass in how not to protect your sensitive information. This is a case study in password security fails. Let’s dissect this double dose of digital danger, shall we? We’ll explore the critical importance of password management and the perils of neglecting basic data protection. We’ll also delve into why these seemingly “convenient” solutions are, in fact, a major cybersecurity nightmare. Act One: The Chronically Insecure “PasswordMonth” Strategy This first act is a classic example of a password security failure. While the intention of changing passwords monthly might seem like a good security practice, the predictable nature of your system completely negates any potential benefit. Here’s why this approach to password security is flawed: Trivial Predictability: Attackers are well aware of common password patterns. Adding a sequential number like the month makes it incredibly easy to guess. Once they crack one month’s password, they have a high probability of predicting future (and potentially past) passwords. This severely undermines your cybersecurity efforts and is a prime example of a password security failure. The problem is that it lacks complexity. A strong password should be a random string of characters, not something that a hacker can easily guess. The Sticky Note Vulnerability: Writing passwords down, especially in plain sight on sticky notes, is akin to handing the keys to your digital kingdom to anyone who walks by. These notes are easily lost, copied, or photographed, creating a significant security risk. It’s hard to overstate how common, and how dangerous, this password security fail is. Lack of Uniqueness: Reusing the base password “password” across all services, even with a monthly number, means that if one account is compromised, all of them are vulnerable. This violates a fundamental principle of effective password management: unique passwords for each account. This is a basic rule of password security. Internal Threat: Disgruntled employees or even cleaning staff could easily gain access to sensitive information with such an insecure system. This highlights the importance of robust internal security protocols. Even with the best intentions, insider threats can exploit weak password security. The Human Factor: Relying on manual monthly updates is prone to error. Employees might forget to change their passwords, use variations, or simply get lazy, further weakening the already flimsy security. Human error is a major contributor to password security fails. Act Two: The “Convenient” Plain Text Password Spreadsheet And now, for the encore of this security circus: the shared spreadsheet of usernames and passwords in plain text. Oh, Sacramento, where do I even begin with this egregious data protection blunder? This takes password security fails to a whole new level. Unencrypted Exposure: Storing passwords in plain text is like keeping the combination to your safe written on the safe itself. Anyone with access to that network drive (internal or external, if your network isn’t properly secured) can see everything. This is a massive cybersecurity vulnerability. It’s a fundamental misunderstanding of password security. Single Point of Failure: If that spreadsheet is compromised (through a network breach, a disgruntled employee, or even accidental deletion without proper backups), your entire company’s digital life is exposed. Proper data backup and recovery procedures are essential to mitigate such risks. This spreadsheet creates a single, catastrophic point of failure for your password security. Audit Trail Nightmare: Who accessed what and when? With a shared, unencrypted spreadsheet, tracking any potential security breaches or unauthorized access becomes virtually impossible. This lack of accountability is a serious security concern. You’d have no way of knowing who accessed this incredibly sensitive data. Ignoring Basic Security Principles: This practice flies in the face of even the most rudimentary data protection guidelines. It screams “we don’t care about security!” to anyone who might be looking. The Gymnarctos Approach to Robust Password Management for Small Businesses Enough with the password security fails! True cybersecurity for small businesses and home users requires a multi-layered approach, starting with secure password management. Let’s talk about how to do password security right. 🔒 Unique, complex passwords for each service: (that aren’t just “password” with sprinkles). These should be a random mix of uppercase and lowercase letters, numbers, and symbols. Aim for a length of at least 12-16 characters. Consider using a strong password generator (like Bitwarden). 🔒 Secure password manager: To store and generate strong credentials, tools like LastPass, 1Password , and Bitwarden offer a way to store your passwords securely, generate strong ones to use elsewhere, and even auto-fill them, eliminating the need for sticky notes and unprotected spreadsheets. These are crucial tools for effective IT support and data protection. We highly recommend exploring these password management solutions. You
Tech Tip Tuesday: The Dark Side of Social Media Security Questions — How a Cute Social Media Game Enables Identity Theft

Introduction “Hello, my lovely technocubbies! Techbear here! Let’s get real about something that might seem like harmless fun: those tempting social media quizzes. You know the ones—they promise to reveal your ‘royal name,’ your ‘dragon name,’ or your ‘celebrity doppelgänger.’ But here’s the truth: social media security questions are often lurking beneath the surface of these quizzes, and they can seriously compromise your online safety.” Honey, sweetie, darling, we need to talk. “I know, I know, it’s easy to get sucked in when you’re bored during a Zoom meeting or just scrolling through your feed. But trust me, these ‘games’ are often digital traps in disguise, and falling for them is like accepting candy from a sketchy van—it might seem appealing, but it can lead to a world of trouble.” Why Are Social Media Security Questions So Dangerous? “Think of social media security questions as the backup keys to your digital life. Websites and apps use them to verify your identity if you forget your password. The problem is that when you happily share answers to these questions on social media, you’re publicly handing over those keys to anyone watching—including hackers.” “It might not seem like a big deal to reveal your first pet’s name or the street you grew up on, but that’s exactly the information cybercriminals seek. They gather these seemingly innocent details from various sources to build a complete profile of you, which then allows them to gain access to your accounts.” What Kind of Information Do These Quizzes Ask For? “Social media security questions often hide within quizzes that ask for apparently harmless details, such as:” “Notice a pattern? These are nearly identical to the questions many websites use for account recovery! Sharing this information publicly makes it incredibly easy for someone to steal your identity.” How Do Hackers Use Social Media Security Questions to Steal Your Identity? “Okay, Techbear, but why should I care? Does anyone really want my stuff?” you might ask. Oh, my sweet, naïve technocubbies, YES! Cybercriminals are absolutely salivating over your information, and here’s why:” “And speaking of email… how many of you still save your ‘account recovery’ information in your email? (Don’t do that, either!)” “And small business owners, listen up! This isn’t just a personal problem. If you or your employees over-share, it can put your entire business at risk.” How to Protect Yourself from Social Media Security Question Scams Alright, enough doom and gloom. Here’s how to fight back against those sneaky social media security questions: Social Media Red Flags: Posts to Avoid “Be extra cautious of any social media posts that ask you to reveal:” These posts are practically screaming, ‘I want to steal your identity!’ Don’t give them the chance. The Final Word from Techbear Okay, I will say it one more time, louder for the people in the back: STOP ANSWERING SOCIAL MEDIA SECURITY QUESTIONS! I know it’s tempting, but the risk is real. If you’ve already shared this information, take action now. Go back and delete those posts. Change your security questions to fake answers (and remember them!). Remember, you’re not just playing a silly game—you’re potentially giving away the keys to your digital kingdom. And Techbear doesn’t want to see that happen. Got questions? Need more help? Ask me in the comments! I’m here for you. You can also contact Gymnarctos Studios for a free 15-minute consultation. About Techbear Greetings, technocubbies! Techbear here, your friendly (and slightly unhinged) neighborhood IT expert. I’m here to make the baffling world of technology accessible to everyone. I’ve seen tech fails you wouldn’t believe are real — routers duct-taped to ceiling fans, email chains longer than the Nile, and enough questionable password choices to make a cybersecurity professional weep. But fear not! I’m here to guide you through the digital wilderness, one absurd analogy and questionable pun at a time. Keywords: social media security questions, social media security, security questions, identity theft, online safety, cybersecurity, password protection, 2FA, social media quizzes, online scams
AI Safety: 7 Essential Strategies That Will Dramatically Transform Your Digital Security
Welcome back to Tech Tip Tuesday, fellow digital explorers! Your favorite tech-savvy bear is here to guide you through the wild woods of artificial intelligence. Grab your honey (or coffee, I don’t judge) and let’s talk AI safety without all the confusing jargon that makes your brain hurt. The AI Revolution: Fantastic or Frightening? Let’s be real: AI tools are EVERYWHERE. They’re writing your emails, generating your social media graphics, and probably planning world domination while you’re reading this. (Kidding! …Maybe.) When talking about AI Safety, one of the most unintentionally perfect metaphors comes from an 1980s fantasy film. In this clip from Return to Oz, TickTock the Clockwork Man’s brain runs down. Like AI systems, he needs human intervention to keep functioning safely. Without it, he hallucinates and spouts gibberish and unpredictable nonsense. As a small business owner or just a regular human trying to survive in this digital jungle, you might be wondering: “TechBear, how do I use these magical AI tools without shooting myself in the paw?” Excellent question, my dear reader! Let’s dive in. 7 AI Safety Tips That Won’t Make Your Eyes Glaze Over 1. Know What You’re Feeding the Machine AI systems learn from the data you provide. Think of them as digital toddlers with photographic memories—they remember EVERYTHING. Never upload sensitive customer information, financial records, or that embarrassing karaoke video from last year’s holiday party. Once it’s in there, consider it potentially exposed. 2. Check the Fine Print (Yes, Actually Read It) I know, I know—terms of service are about as exciting as watching paint dry. But some AI tools claim ownership of anything you create with them. Others might store your inputs for “training purposes.” Take five minutes to skim the privacy policy before uploading your business’s crown jewels. 3. Keep a Human in the Loop AI can make mistakes that are both hilarious and horrifying. That AI-generated email might sound professional until it promises your clients the moon, a pony, and delivery dates that violate the laws of physics. Always review AI-generated content before it goes public. 4. Use Strong Authentication “Password123” isn’t cutting it, Karen. Many AI tools contain valuable data and access. Use long passphrases, two-factor authentication, and consider a password manager. Your future self will thank you when you’re not explaining to clients why your account started sending crypto scams. 5. Be Skeptical of AI-Generated “Facts” AI systems can hallucinate faster than your cousin at Burning Man. They’ll confidently cite non-existent research, invent statistics, and reference products your company never made. Fact-check anything important, especially if it involves numbers, dates, or specific claims. 6. Limit Access and Permissions Not everyone on your team needs the admin keys to your AI kingdom. Set up proper access controls and only give people the permissions they actually need. Your summer intern probably doesn’t require access to generate company financial forecasts. 7. Keep Your AI Tools Updated Just like that smartphone collecting dust in your drawer, AI platforms receive security updates. Make sure you’re running the latest versions and applying patches promptly. Outdated software is basically hanging a “HACK ME” sign on your digital doorstep. The Ethical Minefield of AI Art and Content Now let’s wade into the murky waters of AI ethics. (Don’t worry, I brought ethical floaties!) AI art generators can create stunning visuals faster than you can say “starving artist.” But there’s a catch: these systems were trained on millions of images created by human artists who didn’t necessarily consent to having their work used this way. Similarly, AI writing tools learned from countless human-written articles, books, and posts. When you generate content with AI, are you participating in something problematic? The jury’s still out, but here are some best practices: Recommended External Resources: The Bottom Line AI tools are powerful allies for small businesses when used responsibly. They can help you compete with bigger companies, streamline workflows, and create content more efficiently. But like any tool, they come with risks that require attention. Remember: AI is meant to assist you, not replace your human judgment. Trust your instincts if something feels off, and don’t be afraid to pull the plug if necessary. That’s all for today’s Tech Tip Tuesday! This is TechBear, reminding you that in the tech forest, the prepared survive while the careless get their picnic baskets stolen. Stay safe out there, and see you next week! P.S. If you found these AI safety tips helpful, share them with a friend who still thinks “AI” stands for “Always Impressive” hair styling products. We all know someone. I’m TechBear, the resident IT Bear at Gymnarctos Studios, and your snarky, no-nonsense guide to navigating the digital wilderness. As the self-appointed “papa bear” of the digital world, I protect my technocubbies from the dangers lurking in the tech forest, including the AI wolves and cybersecurity bears that roam the tech forest. When I’m not wrestling rogue algorithms, you might find me optimizing network flow or judging your cable management. (Seriously, folks. It’s a mess!) P.S. Techbear used Claude.ai and ChatGPT to help generate the tips in this post.
