Keep Your Screens Sparkling: TechBear’s Ultimate Guide to Proper Screen Maintenance

Hello, my fabulous and glittery TechnoCubs! It’s your favorite queer-coded IT oracle, Techbear, and today we’re tackling one of the most overlooked tech tasks of them all: proper screen maintenance. Whether you’re a remote-working warrior, a side-hustling star, or just trying to keep your family’s devices from becoming biohazards, knowing how to clean your computer screen, monitor, tablet, or TV the right way is key to making your tech last longer and sparkle like your Aunt Trudy at a rhinestone convention.
The 3-2-1 Backup Rule: The Digital Survival Guide Your Data Is Begging For

What is the 3-2-1 Backup Rule? Listen up, my precious TechnoCubs! Has your digital life ever flashed before your eyes when your laptop decided to play dead? Have you ever felt that stomach-dropping moment when you realized those wedding photos/tax documents/novel-in-progress just vanished into the digital void? If you’ve experienced the special kind of tech horror that is data loss, pull up a chair and get comfortable. Today, Auntie TechBear is serving up the golden standard of data protection: the 3-2-1 backup rule that will save your digital bacon before it gets crispy in all the wrong ways. Backup Bootcamp 101: The 3-2-1 Rule That’ll Save Your Digital Life Let’s get real for a hot second. Your files are precious little digital babies that need protection. Whether it’s work projects that keep you employed, family photos that capture irreplaceable moments, or that screenplay you’ve been tinkering with since 2018, losing them would be somewhere between devastating and catastrophic on the emotional damage scale. The 3-2-1 backup rule isn’t just some tech nerd’s fantasy—it’s a battle-tested strategy recommended by IT professionals who’ve seen things. Horrifying things. Data disasters that would make your hair curl. It’s simple enough for even your technologically-challenged uncle to remember: One Backup Is Like One Potato Chip—Never Enough Think of your backups as a team, each with a specific role in your 3-2-1 backup plan. Relying on a single backup is like driving across the desert with no spare tire and an empty water bottle—a special kind of optimism your fairy godfather of tech cannot endorse. Here’s what the 3-2-1 rule demands: Your Three-Copy Survival Kit Includes: Pro Sass: Think of backups like your emergency honey stash, sweeties. You never want to be caught empty-handed when disaster strikes, looking forlornly at your blank screen while contemplating a career change to something less dependent on technology. Like goat herding. And trust Auntie TechBear when he says those digital disasters don’t care how fierce your outfit is that day! Diversify Your Storage Media Like It’s Your Investment Portfolio The 3-2-1 backup rule emphasizes diversification. Think of your storage media like a collection of precious gems: Variety isn’t just the spice of life—it’s your digital security blanket. Using different storage types protects you from media-specific failures that could otherwise wipe out your entire digital existence. For your two different media types, consider these fabulous options: Don’t Put All Your Digital Eggs in One Ridiculously Fragile Basket My Hot Take: Diversify like you’re managing your retirement fund, honey! Different catastrophes require different protective measures. That’s why the “2” in 3-2-1 deserves your full attention. If your laptop decides today is the day it sacrifices itself to the tech gods, your external drive steps in. If a flood/fire/localized meteor strike damages your home office, your cloud backup is sitting pretty in a server farm somewhere, safe and sound. It’s about creating safety nets for different flavors of digital disasters. “Papa Bear” knows best for keeping your precious data safe from harm. Offsite Backup: Your Long-Distance Relationship with Data The “1” in the 3-2-1 rule is the cherry on top of your backup sundae. Your offsite backup—typically cloud storage—is your long-distance relationship with your data. When local disasters strike (theft, fire, that coffee spill that somehow defies the laws of physics), you’ll be thanking me with chocolates and flowers. Cloud storage options like iDrive, Carbonite, or Microsoft OneDrive make offsite backups easier than ordering takeout. Tough Love Tip: TEST YOUR BACKUPS QUARTERLY, OR ELSE Nothing says “tech fail” quite like discovering your backup is as useful as a chocolate teapot when you actually need it. That smug feeling of “I have backups!” evaporates pretty quickly when those backups turn out to be corrupted, incomplete, or from 2019. Your tech guardian angel is wagging his finger at you right now: Schedule quarterly checks—mark them in your calendar with alarm bells and flashing lights if needed—to ensure your backups are actually working: Remember: Data Loss Is for the Unprepared. And Darling, You’re Too Fabulous to Be Unprepared. Data loss isn’t a matter of if—it’s a matter of when. Hard drives fail with the predictability of a reality TV drama. Accidents happen. Ransomware attacks are increasingly common. And sometimes we make mistakes and delete things we absolutely, positively should not have deleted. The good news? With the 3-2-1 backup rule, you’re prepared for almost any data disaster that comes your way, strutting through potential catastrophes with the confidence of someone who knows their digital life is secure in triplicate. Getting Started with Your 3-2-1 System (Because There’s No Time Like Right Now) Ready to implement the 3-2-1 rule before disaster strikes? Here’s how to begin: For more detailed guides on setting up specific backup solutions, check out my Ultimate Backup Guide for Beginners, where I walk you through each step with minimal technical jargon and maximum hand-holding. Mother TechBear didn’t raise no fools, and I won’t let my cubs flounder in the digital wilderness! What’s your backup strategy looking like? Have you had a close call with data loss that still gives you nightmares? Share your horror stories in the comments—we can all learn from each other’s digital trauma! Additional Resources For my TechnoCubs looking to protect their digital lives with the 3-2-1 backup rule, here are some helpful resources: Backblaze’s Guide to the 3-2-1 Backup Strategy – A straightforward explanation with practical implementation tips World Backup Day – Simple resources and reminders about the importance of backups (perfect for beginners) Wirecutter’s Best External Hard Drives – Consumer-friendly reviews to help you choose reliable backup hardware PCMag’s Cloud Backup Service Comparison – Find the right cloud solution for your offsite backup needs How to Create a Simple Backup Plan: Consumer Reports’ Easy-to-Follow Guide for Non-Technical Users Need Personalized Backup Guidance? Still feeling overwhelmed by backup options? Not sure if your current setup follows the 3-2-1 rule properly? At Gymnarctos Studios, we understand that every digital life is unique. Contact us today at gymnarctosstudiosllc@gmail.com for a
Ask Tech Bear: Password Security Fails — A Cybersecurity Comedy of Errors
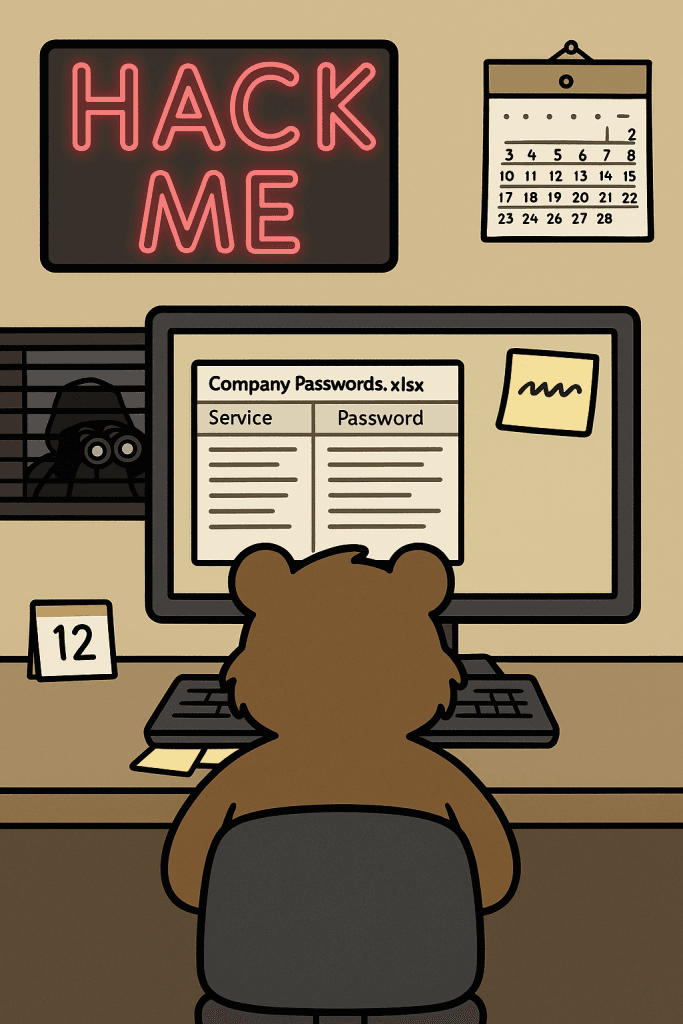
We’ve all heard about password security fails, but this week’s letter takes the cake. It’s a wild ride through a landscape of truly terrible password practices, and it’s a stark reminder of why small business cybersecurity is so crucial. Dear Tech Bear, I’ve created the perfect password system, but my former IT guy said these practices are a password security failure. All of our company passwords are “password” followed by the current month number. We change them monthly for security! Plus, I’ve created a shared spreadsheet on my company’s network drive so everyone can see it. It was a hassle having to remember a password to open it, so I just left it in plain text. My IT support guy quit last week for unrelated reasons. Before the spreadsheet, everyone just wrote their passwords on sticky notes and put them under the keyboard or stuck them on their monitor. I think the spreadsheet is a security improvement. How impressed should I be with myself? Security Genius in Sacramento Oh my sweet summer child… Your “perfect” password system isn’t security—it’s a welcome mat for hackers with a calendar and a treasure map! And those sticky notes? Might as well put up a billboard with your bank account details, illuminated by a flashing neon sign that reads “Easy Access!” In the digital wilderness of small business cybersecurity, your current strategy isn’t just flawed; it’s a masterclass in how not to protect your sensitive information. This is a case study in password security fails. Let’s dissect this double dose of digital danger, shall we? We’ll explore the critical importance of password management and the perils of neglecting basic data protection. We’ll also delve into why these seemingly “convenient” solutions are, in fact, a major cybersecurity nightmare. Act One: The Chronically Insecure “PasswordMonth” Strategy This first act is a classic example of a password security failure. While the intention of changing passwords monthly might seem like a good security practice, the predictable nature of your system completely negates any potential benefit. Here’s why this approach to password security is flawed: Trivial Predictability: Attackers are well aware of common password patterns. Adding a sequential number like the month makes it incredibly easy to guess. Once they crack one month’s password, they have a high probability of predicting future (and potentially past) passwords. This severely undermines your cybersecurity efforts and is a prime example of a password security failure. The problem is that it lacks complexity. A strong password should be a random string of characters, not something that a hacker can easily guess. The Sticky Note Vulnerability: Writing passwords down, especially in plain sight on sticky notes, is akin to handing the keys to your digital kingdom to anyone who walks by. These notes are easily lost, copied, or photographed, creating a significant security risk. It’s hard to overstate how common, and how dangerous, this password security fail is. Lack of Uniqueness: Reusing the base password “password” across all services, even with a monthly number, means that if one account is compromised, all of them are vulnerable. This violates a fundamental principle of effective password management: unique passwords for each account. This is a basic rule of password security. Internal Threat: Disgruntled employees or even cleaning staff could easily gain access to sensitive information with such an insecure system. This highlights the importance of robust internal security protocols. Even with the best intentions, insider threats can exploit weak password security. The Human Factor: Relying on manual monthly updates is prone to error. Employees might forget to change their passwords, use variations, or simply get lazy, further weakening the already flimsy security. Human error is a major contributor to password security fails. Act Two: The “Convenient” Plain Text Password Spreadsheet And now, for the encore of this security circus: the shared spreadsheet of usernames and passwords in plain text. Oh, Sacramento, where do I even begin with this egregious data protection blunder? This takes password security fails to a whole new level. Unencrypted Exposure: Storing passwords in plain text is like keeping the combination to your safe written on the safe itself. Anyone with access to that network drive (internal or external, if your network isn’t properly secured) can see everything. This is a massive cybersecurity vulnerability. It’s a fundamental misunderstanding of password security. Single Point of Failure: If that spreadsheet is compromised (through a network breach, a disgruntled employee, or even accidental deletion without proper backups), your entire company’s digital life is exposed. Proper data backup and recovery procedures are essential to mitigate such risks. This spreadsheet creates a single, catastrophic point of failure for your password security. Audit Trail Nightmare: Who accessed what and when? With a shared, unencrypted spreadsheet, tracking any potential security breaches or unauthorized access becomes virtually impossible. This lack of accountability is a serious security concern. You’d have no way of knowing who accessed this incredibly sensitive data. Ignoring Basic Security Principles: This practice flies in the face of even the most rudimentary data protection guidelines. It screams “we don’t care about security!” to anyone who might be looking. The Gymnarctos Approach to Robust Password Management for Small Businesses Enough with the password security fails! True cybersecurity for small businesses and home users requires a multi-layered approach, starting with secure password management. Let’s talk about how to do password security right. 🔒 Unique, complex passwords for each service: (that aren’t just “password” with sprinkles). These should be a random mix of uppercase and lowercase letters, numbers, and symbols. Aim for a length of at least 12-16 characters. Consider using a strong password generator (like Bitwarden). 🔒 Secure password manager: To store and generate strong credentials, tools like LastPass, 1Password , and Bitwarden offer a way to store your passwords securely, generate strong ones to use elsewhere, and even auto-fill them, eliminating the need for sticky notes and unprotected spreadsheets. These are crucial tools for effective IT support and data protection. We highly recommend exploring these password management solutions. You
Ditch the Digital Drudgery: 4 Simple Automation Tools That Won’t Make Your Head Explode

Overwhelmed by tech tasks? Techbear’s got your back! Discover simple automation tools that even you can use. Reclaim your sanity now!
Maintenance Monday: The Great Upgrade or Repair Showdown
Upgrade or repair: TechBear’s 7-step guide helps home users and small businesses make smart tech decisions. Save money and avoid costly mistakes with our practical approach to tech maintenance.
Ask The TechBear: 2 Small Business Cybersecurity Dilemmas, 1 Simple Solution

Hello, my fabulous technocubs! Tech Bear here, ready to untangle your small business cybersecurity dilemmas. This week, we have a double dose of security snafus, proving that when it comes to online safety, folks tend to swing from one extreme to the other. Small business cybersecurity is no laughing matter, but sometimes the ways people get it wrong are… well, let’s just say they provide excellent material for your favorite TechBear! Let’s dive into these tech troubles, shall we? Small Business Cybersecurity Dilemma # 1: Security? What’s That? Dear Tech Bear, I’ve streamlined our security for maximum efficiency! Our password is “password” plus the month (e.g., password4), and they’re all on sticky notes under the keyboards. Nobody has time for complicated passwords! We also use the free antivirus that came with the computers—it’s free, so it’s gotta be good, right? And updates? Ain’t nobody got time for that! We’re too small to be hacked anyway. Hackers only go after the big guys. – Efficiently Insecure Small Business Cybersecurity Dilemma #2: Security Overkill Dear Tech Bear, I take security very seriously. I’ve installed three different antivirus suites on my laptop, along with two third-party firewall programs and a VPN that’s always on. Now, my computer runs slower than molasses in January. But hey, at least I’m safe, right? – Paranoia Strikes * * * Oh, my sweet summer children!… I’m dealing with two extremes of the small business cybersecurity spectrum today, and honestly, both are equally concerning! To Efficiently Insecure: I’m not sure whether to laugh or cry. Your security system is so bad it’s circled back to being hilarious, but the potential consequences for your small business are definitely not funny. Let’s break down this horror show, shall we? Because honey, you’re practically waving a neon sign inviting cyber trouble: To Paranoia Strikes: There’s a difference between being secure and building a digital Great Wall of China around your laptop. While I commend your diligence, you’ve gone overboard, and it’s actually hindering your productivity. Small business cybersecurity is about balance, not overkill. Here’s the diagnosis: Our suggestions: The Gymnarctos Security Essentials The Gymnarctos Security Essentials (for both of you!): ✅ Strong, unique passwords + password manager: For Efficiently Insecure, this is non-negotiable. Strong passwords are the foundation of small business cybersecurity. Use a mix of uppercase and lowercase letters, numbers, and symbols. And for goodness sake, use a password manager to store them securely! ✅ One reliable antivirus: Choose a reputable antivirus program and keep it updated. For Paranoia Strikes, uninstall the redundant programs. Small business cybersecurity is about quality, not quantity. ✅ Firewall + regular updates: Ensure your built-in firewall is turned on and configured correctly. And for both of you, PLEASE, for the love of all that is holy in the tech world, install those updates! They are crucial for small business cybersecurity. ✅ Security awareness training: Educate yourself and your employees about common threats like phishing, malware, and social engineering. Human error is a major factor in small business cybersecurity breaches. ✅ Regular maintenance: Keep your systems clean, patched, and running smoothly. This includes everything from software updates to hardware maintenance. Proactive maintenance is key to small business cybersecurity. ✅ VPN (when needed, like on public Wi-Fi): A VPN is a valuable tool, especially when accessing sensitive data on unsecured networks. But it’s not always necessary to have it running 24/7. Use it strategically as part of your overall small business cybersecurity plan. Additional Resources: Your Small Business Cybersecurity Toolkit Alright, my lovelies, you’ve heard TechBear’s wisdom, and now it’s time to arm yourselves! Here’s a handy list of tools and tips to boost your small business cybersecurity. Remember, no single tool is a silver bullet; it’s all about a layered approach and good habits! (Neither Gymnarctos Studios nor Ask the TechBear are sponsored by or affiliated with any of these products. They are simply well-regarded in the field) I. Password Managers: II. Antivirus: III. VPNs IV. Mobile Device Security: Important Note: These are just a few suggestions, my dears. The best security setup depends on your specific needs and setup. Do your research, stay informed, and never stop learning about small business cybersecurity! Small business cybersecurity is crucial, but it shouldn’t be a source of constant anxiety or a performance bottleneck. It’s about finding the right balance between protection and usability. Let’s work together to find your sweet spot and keep your business safe! #CyberSecurityFails #PasswordSecurity #SmallBusinessSecurity #TechSupport #PerformanceIssues #SmallBusinessIT #SmallBusinessCybersecurity
10 Brilliant Ways to Create Effective Task Reminders That You Won’t Ignore: The Techbear Guide to Actually Getting Stuff Done

Listen up, productivity wannabes. Creating effective task reminders is the difference between actually getting things done and drowning in a sea of forgotten obligations. If your current reminder system consists of 47 sticky notes slowly peeling off your monitor and a vague sense of impending doom, this one’s for you. Today we’re diving into the world of effective task reminders that actually remind you of things instead of becoming digital clutter you’ve mastered the art of ignoring. Why Your Current Reminder System Is Failing Miserably Let’s be honest—if your phone is constantly buzzing with notifications you immediately swipe away without reading, you might as well just throw your device into the nearest body of water. It would be equally effective and more dramatic. The average human attention span is now shorter than a goldfish’s, which explains why you’ve probably forgotten what this article is about three times already. Welcome back, by the way. Way #1: Make Your Reminders Ridiculously Specific Setting effective task reminders starts with specificity. “Follow up” is not a reminder. It’s a wish upon a star. Try something radical like “Email Sarah about Q2 report corrections by 2 PM Tuesday” instead. Research shows that implementation intentions (the fancy term for specific when-then plans) make you 2-3 times more likely to actually do the thing. The formula for a specific reminder is brutally simple: What + When + Where + How. If your reminder doesn’t answer these questions, it’s about as useful as a chocolate teapot. Further Reading: The Science of Implementation Intentions Way #2: Harness the Power of Location-Based Triggers Your brain isn’t wired to remember random tasks at random times—it’s wired to remember contextual cues. That’s why you walk into the kitchen and immediately forget why you went there. Setting up location-based reminders that ping you when you arrive at specific places is basically outsourcing your memory to robots. “Remind me to pick up printer paper when I’m near Office Depot” is significantly more useful than “buy paper sometime maybe.” Pro tip: Set exit reminders too. “Don’t forget your umbrella when leaving the office” has saved countless technocubbies from getting drenched because their predictably forgetful brains were too busy thinking about happy hour. Further Reading: How Geofencing Makes Reminders Actually Work Way #3: Schedule Reminders When Your Brain Actually Works Creating effective task reminders means timing them properly. Scheduling a reminder to “start that massive project” at 4:45 PM on a Friday is self-sabotage at its finest. According to research on biological prime time, most humans have peak focus periods in the late morning and late afternoon. Schedule your most brain-intensive reminders accordingly, or accept your fate as an eternal procrastinator. Map your energy levels for a week (yes, an actual week, not just your theoretical best day) and schedule reminders to tackle complex tasks during your high-energy windows. Save your low-energy periods for reminders about mindless tasks like “organize your digital sock drawer” or “like your boss’s cringey LinkedIn posts.” Further Reading: When: The Scientific Secrets of Perfect Timing Way #4: Transform Your Phone’s Default Reminder App Let’s talk about the elephant in the room: your phone’s built-in reminder app probably sucks. But with a few tweaks, you can make those default phone reminders actually useful. The key to effective task reminders on your phone is customization. Use different alert sounds for different priority levels. Set recurring reminders for habits you’re building. And for heaven’s sake, turn on badge notifications instead of relying on those easily-dismissed banners that you’ll ignore faster than emails from your college alumni association. For iPhone users: Did you know you can set reminders based on when you message someone? “Remind me about the project deadline next time I text Dave” is the passive-aggressive productivity hack you didn’t know you needed. For Android users: Smart reminders that bundle with related apps (like Grocery reminders showing up when you open your grocery list app) are a game-changer for context-switching disasters like your brain. Further Reading: Hidden Features in iOS Reminders | Google Keep’s Secret Power Features Way #5: Use the Two-Minute Rule to Avoid Reminder Overload Here’s the dirty little secret reminder apps don’t want you to know: the best reminder system is the one you’ll actually use consistently. Groundbreaking, I know. If you’re constantly ignoring your reminders, try the two-minute rule: If a task takes less than two minutes, do it immediately instead of setting a reminder. For everything else, create effective task reminders that pass what I call the “Future You Test”—would your tired, annoyed future self actually understand and appreciate this reminder, or will they hate Past You for being vague and unhelpful? Your reminder app should not be a graveyard for tasks you’re avoiding. It should be a trusted system that helps you, not a digital representation of your mounting anxiety. Further Reading: Getting Things Done: The Art of Stress-Free Productivity Way #6: Apply the “Future You Test” for Every Reminder Ever set a reminder that says “Important thing!!!” only to have no clue what that important thing was when it pops up? Congratulations, you’ve failed the Future You Test. Creating effective task reminders means considering your future mental state. Future You will have forgotten the context, the urgency, and probably what day it is. Future You is basically a confused golden retriever wearing your clothes. Include enough context that Future You doesn’t curse Past You’s name. Add links to relevant files, include phone numbers you’ll need, specify exactly which “John” you’re supposed to call (Work John? Neighbor John? John who owes you money?). Better yet, write reminders with empathy for your future self: “Call insurance – have policy number ready (in Notes app), call before 5pm EST, estimated call time: 15 min, reward self with cookie afterward.” Further Reading: The Present Bias: Why Your Future Self Doesn’t Stand a Chance Way #7: Master the Art of Priority Coding Not all reminders are created equal. “Buy milk” and “Submit tax documents before audit deadline” probably shouldn’t have
AI Safety: 7 Essential Strategies That Will Dramatically Transform Your Digital Security
Welcome back to Tech Tip Tuesday, fellow digital explorers! Your favorite tech-savvy bear is here to guide you through the wild woods of artificial intelligence. Grab your honey (or coffee, I don’t judge) and let’s talk AI safety without all the confusing jargon that makes your brain hurt. The AI Revolution: Fantastic or Frightening? Let’s be real: AI tools are EVERYWHERE. They’re writing your emails, generating your social media graphics, and probably planning world domination while you’re reading this. (Kidding! …Maybe.) When talking about AI Safety, one of the most unintentionally perfect metaphors comes from an 1980s fantasy film. In this clip from Return to Oz, TickTock the Clockwork Man’s brain runs down. Like AI systems, he needs human intervention to keep functioning safely. Without it, he hallucinates and spouts gibberish and unpredictable nonsense. As a small business owner or just a regular human trying to survive in this digital jungle, you might be wondering: “TechBear, how do I use these magical AI tools without shooting myself in the paw?” Excellent question, my dear reader! Let’s dive in. 7 AI Safety Tips That Won’t Make Your Eyes Glaze Over 1. Know What You’re Feeding the Machine AI systems learn from the data you provide. Think of them as digital toddlers with photographic memories—they remember EVERYTHING. Never upload sensitive customer information, financial records, or that embarrassing karaoke video from last year’s holiday party. Once it’s in there, consider it potentially exposed. 2. Check the Fine Print (Yes, Actually Read It) I know, I know—terms of service are about as exciting as watching paint dry. But some AI tools claim ownership of anything you create with them. Others might store your inputs for “training purposes.” Take five minutes to skim the privacy policy before uploading your business’s crown jewels. 3. Keep a Human in the Loop AI can make mistakes that are both hilarious and horrifying. That AI-generated email might sound professional until it promises your clients the moon, a pony, and delivery dates that violate the laws of physics. Always review AI-generated content before it goes public. 4. Use Strong Authentication “Password123” isn’t cutting it, Karen. Many AI tools contain valuable data and access. Use long passphrases, two-factor authentication, and consider a password manager. Your future self will thank you when you’re not explaining to clients why your account started sending crypto scams. 5. Be Skeptical of AI-Generated “Facts” AI systems can hallucinate faster than your cousin at Burning Man. They’ll confidently cite non-existent research, invent statistics, and reference products your company never made. Fact-check anything important, especially if it involves numbers, dates, or specific claims. 6. Limit Access and Permissions Not everyone on your team needs the admin keys to your AI kingdom. Set up proper access controls and only give people the permissions they actually need. Your summer intern probably doesn’t require access to generate company financial forecasts. 7. Keep Your AI Tools Updated Just like that smartphone collecting dust in your drawer, AI platforms receive security updates. Make sure you’re running the latest versions and applying patches promptly. Outdated software is basically hanging a “HACK ME” sign on your digital doorstep. The Ethical Minefield of AI Art and Content Now let’s wade into the murky waters of AI ethics. (Don’t worry, I brought ethical floaties!) AI art generators can create stunning visuals faster than you can say “starving artist.” But there’s a catch: these systems were trained on millions of images created by human artists who didn’t necessarily consent to having their work used this way. Similarly, AI writing tools learned from countless human-written articles, books, and posts. When you generate content with AI, are you participating in something problematic? The jury’s still out, but here are some best practices: Recommended External Resources: The Bottom Line AI tools are powerful allies for small businesses when used responsibly. They can help you compete with bigger companies, streamline workflows, and create content more efficiently. But like any tool, they come with risks that require attention. Remember: AI is meant to assist you, not replace your human judgment. Trust your instincts if something feels off, and don’t be afraid to pull the plug if necessary. That’s all for today’s Tech Tip Tuesday! This is TechBear, reminding you that in the tech forest, the prepared survive while the careless get their picnic baskets stolen. Stay safe out there, and see you next week! P.S. If you found these AI safety tips helpful, share them with a friend who still thinks “AI” stands for “Always Impressive” hair styling products. We all know someone. I’m TechBear, the resident IT Bear at Gymnarctos Studios, and your snarky, no-nonsense guide to navigating the digital wilderness. As the self-appointed “papa bear” of the digital world, I protect my technocubbies from the dangers lurking in the tech forest, including the AI wolves and cybersecurity bears that roam the tech forest. When I’m not wrestling rogue algorithms, you might find me optimizing network flow or judging your cable management. (Seriously, folks. It’s a mess!) P.S. Techbear used Claude.ai and ChatGPT to help generate the tips in this post.
Ask TechBear: 4 Recommendations for Home WiFi Network Solutions That Won’t Leave Your Budget Spinning

‘Ask Tech Bear’ addresses technology troubles with a humorous touch, focusing this week on misusing a ceiling fan for router placement. Key issues include physical damage, signal inconsistency, overheating, and security risks. Proper router placement and professional WiFi solutions ensure optimal performance, emphasizing the importance of safe networking practices for home and business use.
Two-Factor Authentication (2FA): Our Essential Tech Tip Tuesday Guide for Smartly Securing Your Accounts
Passwords Aren’t Enough! Why You Need Two-Factor Authentication (2FA) Right Now Alright, listen up, my fabulous tech cubs. What the heck is two-factor authentication (2FA)? I’m glad you asked. If you’re still walking around the internet with just a password protecting your accounts, honey, you might as well be leaving your front door wide open with a neon sign that says, “Come on in, hackers!” 🚨 Passwords alone aren’t enough anymore. Cybercriminals have all sorts of sneaky tricks—phishing emails, credential stuffing, brute force attacks—to get into your accounts. And let’s be real: if your password is something like password123 or Fluffy1997, sweetie, you’re basically handing them the keys. That’s where 2FA swoops in like a fabulous, high-tech security blanket. What Is Two-Factor Authentication? Two-factor authentication (2FA) is a simple yet powerful security measure that requires two different forms of verification to log into an account. Instead of just entering a password, you also need a second factor, like a one-time code or a biometric scan. Think of it like this: If your password is the lock on your front door, then 2FA is the deadbolt, security camera, and guard dog all in one. 🐻🔒 Types of Two-Factor Authentication Not all 2FA methods are created equal. Choosing the right two-factor authentication (2FA) method depends on your needs, tech comfort level, and security priorities. Let’s break it down in plain English, so you can pick the best option for you and your business. 1️⃣ SMS Codes (Text Message Authentication) How it works: When you log in, a code is sent to your phone via text. You enter the code to confirm your identity. ✅ Pros:✔️ Super easy to set up—just link your phone number.✔️ No need to install extra apps or buy anything.✔️ Better than relying on just a password. ❌ Cons:🚨 Hackable via SIM-swapping attacks—hackers can trick your phone carrier into transferring your number to their device.📶 Requires a cell signal, so it won’t work in areas with poor reception.📱 Tied to your phone number, so if you lose your phone or change numbers, you might get locked out. 👨💼 Best for: Home users who need a basic security boost but don’t want to deal with apps. 2️⃣ Authenticator Apps (The Recommended Option!) How it works: You install an app like Google Authenticator, Microsoft Authenticator, or Authy. It generates a time-sensitive, one-time-use code when you log in. ✅ Pros:✔️ Much more secure than SMS—codes are generated locally on your phone, not sent over the internet.✔️ No risk of SIM-swapping attacks since it doesn’t rely on your phone number.✔️ Works even without a cell signal (as long as your phone is on).✔️ Free to use and widely supported. ❌ Cons:📲 You must have your phone with you to log in.🔑 If you lose your phone, you need backup codes or a recovery method (which many people forget to set up).📌 Not as easy to set up as SMS, but still pretty user-friendly. 👨💼 Best for: Small businesses, home users, and anyone looking for a strong, reliable security option without extra costs. 🔹 Pro Tip: If you use an authenticator app, store your backup codes somewhere safe! If you lose access to your phone, these codes will save you. 3️⃣ Hardware Security Keys (The Gold Standard for Security) How it works: You plug in a USB key (like YubiKey or Google Titan) or tap a wireless NFC key to verify your identity. ✅ Pros:✔️ Virtually unhackable—no phishing, no SIM-swapping, no password leaks.✔️ No need to remember or type codes—just plug in the key and go.✔️ Works offline and doesn’t require a phone.✔️ Great for business security, especially for employees handling sensitive data. ❌ Cons:💰 Costs money—usually between $20–$60 per key, depending on the brand and features.🔑 You must keep track of the physical key—lose it, and you’ll need a backup.📌 Not as widely supported as other methods (though adoption is growing). 👨💼 Best for: Small businesses, IT professionals, and high-risk users (like financial managers, journalists, and executives). 🔹 Pro Tip: If you go this route, buy two security keys—one as a backup in case you lose the main one. 4️⃣ Biometric Authentication (Your Face or Fingerprint) How it works: You log in using Face ID, fingerprint scanners, or retina scans—no passwords or codes required. ✅ Pros:✔️ Super convenient—just scan your face or finger.✔️ Fastest way to log in.✔️ Hard to steal—hackers can’t “guess” your fingerprint. ❌ Cons:🤷 Not all websites support biometric login yet.🔄 You might need a backup method (like an authenticator app or password).📌 Could be bypassed with a stolen or cloned fingerprint (though rare). 👨💼 Best for: Home users and small businesses already using smartphones with biometric security. 🔹 Pro Tip: Use biometrics alongside another 2FA method, not as your only protection. Which 2FA Method Should You Use? 2FA Type Security Level Ease of Use Best For SMS Codes ⭐⭐☆☆☆ (OK) ⭐⭐⭐⭐☆ (Easy) Home users, beginners Authenticator App ⭐⭐⭐⭐☆ (Good) ⭐⭐⭐☆☆ (Moderate) Small businesses, tech-savvy users Security Keys ⭐⭐⭐⭐⭐ (Best) ⭐⭐☆☆☆ (Harder) High-risk users, businesses Biometrics ⭐⭐⭐⭐☆ (Good) ⭐⭐⭐⭐⭐ (Easiest) Smartphone users, convenience seekers Which One is Right for You? 🔹 If you’re not super techy, start with SMS-based 2FA—it’s better than nothing!🔹 If you want strong security, use an authenticator app like Google Authenticator.🔹 If you run a small business, consider security keys for ultimate protection.🔹 If you love convenience, enable biometric authentication where possible. 💡 Best Practice: Use multiple 2FA methods whenever possible. For example, use an authenticator app as your primary method and keep a security key or backup codes in case you lose your phone. Why You Need 2FA (Like, Yesterday) Still not convinced? Here’s why enabling two-factor authentication is non-negotiable: 🚫 Stops Password Leaks in Their TracksEven if a hacker steals your password, they still need the second factor to get in. 🛡️ Protects Against Phishing & Credential TheftPhishing emails are getting sneaky, but without your second factor, hackers hit a dead end. 💰 Safeguards Your Finances & IdentityBank accounts, cryptocurrency wallets, PayPal—without 2FA,
