“Computer Repair Minneapolis”—Or The Hard Truth About Why Your Website Isn’t The “Field of Dreams”
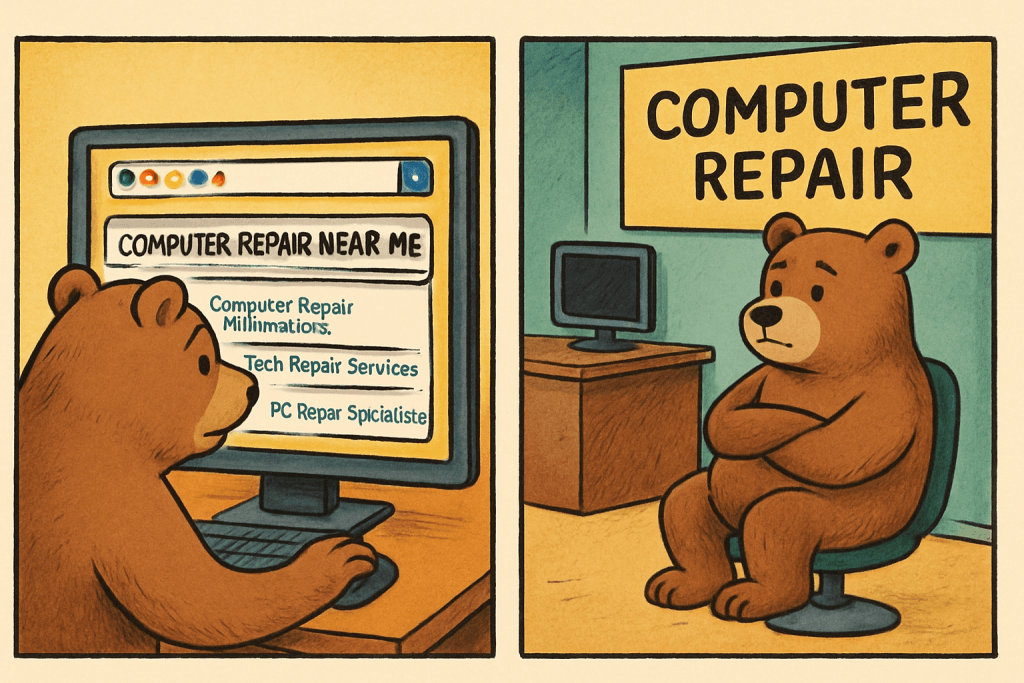
From invisible to searchable: Follow TechBear’s honest journey as Gymnarctos Studios discovers why ‘computer repair Minneapolis’ searches weren’t finding their business—and the fixes that actually work.
Tech Tip Tuesday: Digital Wellbeing Made Simple – TechBear’s 5-Step Framework for Healthier Screen Habits

Feeling overwhelmed by the digital jungle? 📱💻 Don’t let your tech turn into a techno-beast! 🐻✨ Your friendly neighborhood TechBear is here with a simple, 5-step guide to digital wellbeing. Learn how to tame your screen time, discover hidden tools you’re already paying for, and create healthier tech habits today. Let’s make technology work for you, not against you! Ready to find your digital balance? Click here to learn more! #DigitalWellbeing #ScreenTimeManagement #TechBear
Tech Tip Tuesday: 10 Hidden Smartphone Features Your Device Can Already Do (But No One Told You!)

Techbear is back to dish the juicy dirt on 10 mind-blowing hidden smartphone features that will not only impress your friends but also simplify your life! Discover how your phone can transform into a boss-level scanner, a real-time translator that speaks every language, a personal audiobook narrator for tired eyes, and so much more untapped power in your pocket. Get ready to unlock the secret potential of that glorious gadget! #HiddenFeatures #PhoneTricks #UnlockPhonePotential #MobileDeviceCapabilities #SecretPhoneFunctions #ProductivityHacks
Keyboard Shortcuts That Actually Save Time: Stop Clicking Around Like a Lost Tourist

Let’s be real. Watching someone navigate their computer with only a mouse in 2025 is like watching someone try to pay for groceries with seashells. Cute, maybe, in a prehistoric sort of way. Efficient? Honey, no. That’s where keyboard shortcuts swoop in like the superheroes of productivity (minus the spandex, thankfully). These time-saving shortcuts might seem insignificant on their own, but trust your old pal Techbear, the seconds add up when you use these productivity shortcuts consistently. These essential keyboard shortcuts are the secret weapon that productivity experts have been using for years, and it’s time everyone learned them. Lane et al. (2005) conducted a study on experienced Microsoft Word users and found that even proficient individuals often overlooked essential keyboard shortcuts in favor of less efficient methods like icon toolbars[cite: 5, 39]. This highlights the substantial productivity benefits of mastering keyboard shortcuts over relying solely on graphical interfaces[cite: 1]. The Cold, Hard Truth: Time Study Results You Can Actually Understand Lane et al. (2005) rigorously compared the efficiency of issuing commands using keyboard shortcuts versus mouse-based methods (icon toolbars and menus)[cite: 80]. To illustrate the time savings, consider the following data extracted from their research: Task Keyboard Shortcut Time Icon Toolbar Time Menu Time Copy Text 1.35 2.27 2.93 Paste Text 1.67 2.08 3.09 Save Document 1.40 2.15 2.75 Open Document 1.33 1.95 2.60 The research clearly demonstrates that keyboard shortcuts consistently outperform mouse navigation across all common tasks. Learning these productivity shortcuts represents one of the highest-ROI investments you can make in your digital workflow. As you can clearly see, keyboard shortcuts consistently outperform their mouse-driven counterparts. For instance, the average time to copy text using keyboard shortcuts was a mere 1.35 seconds, compared to 2.27 seconds using the icon toolbar and a whopping 2.93 seconds using the menu[cite: 93, 99]. Similarly, pasting text took only 1.67 seconds with shortcuts, while the icon toolbar and menu methods dragged behind at 2.08 seconds and 3.09 seconds, respectively[cite: 93, 99]. Essential Keyboard Shortcuts Everyone Should Know Before diving into advanced techniques, let’s establish the foundational keyboard shortcuts that every computer user should master. These fundamental shortcuts work across most applications and will immediately boost your productivity: Mastering just these five basic productivity shortcuts will noticeably speed up your daily workflow. The Sneaky Power of Compounding (Prepare for Your Jaw to Drop) Let’s say you perform these four basic tasks (copy, paste, save, open) just ten times a day. And the time savings are even more dramatic when compared to using menus! Over a year, we’re talking about potentially saving hours. Hours you could be spending on, you know, actually important things. Like perfecting your sourdough starter or finally figuring out TikTok dances. Level Up Your Shortcut Game: Creating Your Own Power Moves The pre-programmed shortcuts are great and all, but what if you want to be truly efficient? Good news, my friend! Both Windows and macOS let you create custom keyboard shortcuts. It’s like having your own secret code to computer wizardry. Creating custom keyboard shortcuts tailored to your specific workflow can take your productivity to even greater heights. You can personalize Windows and Mac shortcuts to match your exact needs. For the Windows Warriors: Important Note for Windows: Custom shortcuts created this way usually only work when the application is open. For system-wide shortcuts, you might need to delve into third-party tools, but let’s not scare our tech novices just yet. Baby steps, people! For more in-depth information, check out Learn how to create keyboard shortcuts in Windows. For the Mac Mavericks: For a more visual guide, Apple has you covered: Create keyboard shortcuts for apps on Mac. Pro Tip for Everyone: When creating custom shortcuts, try to choose combinations that are easy to remember and don’t conflict with existing shortcuts. A little logic goes a long way!</div> Supercharge Your Workflow: Essential Keyboard Shortcuts for Everyday Apps Let’s be real, there are some shortcuts that are just non-negotiable. Commit these to memory, and you’ll instantly feel like you’ve leveled up your tech game. These productivity shortcuts represent the minimum set of keyboard shortcuts every computer user should memorize. Web Browsers (Chrome, Firefox, Edge): Microsoft Office (Word, Excel, PowerPoint): File Explorer (Windows) / Finder (Mac): For the Truly Dedicated: Exploring Shortcut Manager Tools For the truly power-hungry (and slightly more adventurous) among you, there are tools that let you create custom shortcuts for just about anything. On Windows, AutoHotkey is a popular (and free!) option, while Mac users might want to check out BetterTouchTool. Just be warned, with great power comes great responsibility (and maybe a little bit of a learning curve). Mobile Shortcuts Magic: Make Siri and Google Assistant Work Harder for You While you might not have the traditional “Ctrl+C” on your phone, both iOS and Android offer clever ways to speed things up, often leveraging the power of your voice. Let’s dive into these essential mobile shortcuts! iOS Shortcuts: Siri’s Got Your Back (and Your Apps) Apple’s “Shortcuts” app is a game-changer for automation. It lets you create custom workflows that can be triggered with a tap, a widget, or (you guessed it) your voice via Siri. Android Shortcuts: “Hey Google, Do Your Thing!” Android also offers robust voice command capabilities through Google Assistant, along with app-specific shortcuts and accessibility features. Pro Tip for the Mobile Crowd: Spend a few minutes exploring the Shortcuts app on iOS or the Routines in Google Home. You’ll be surprised at how much time you can save by automating everyday tasks with just your voice! Techbear’s Bonus Goodies Feeling overwhelmed? Don’t fret! Techbear’s whipped up a handy-dandy cheat sheet of the most essential keyboard shortcuts for both Windows and macOS. Download it here and keep it close – your wrists will thank you! Want even more time-saving wisdom? Follow Techbear on your favorite social media platform for our weekly “Shortcut of the Week” tip! Techbear’s Parting Shot (Because I Care, Deep Down) Look, learning a bunch of shortcuts might seem
AI Safety: 7 Essential Strategies That Will Dramatically Transform Your Digital Security
Welcome back to Tech Tip Tuesday, fellow digital explorers! Your favorite tech-savvy bear is here to guide you through the wild woods of artificial intelligence. Grab your honey (or coffee, I don’t judge) and let’s talk AI safety without all the confusing jargon that makes your brain hurt. The AI Revolution: Fantastic or Frightening? Let’s be real: AI tools are EVERYWHERE. They’re writing your emails, generating your social media graphics, and probably planning world domination while you’re reading this. (Kidding! …Maybe.) When talking about AI Safety, one of the most unintentionally perfect metaphors comes from an 1980s fantasy film. In this clip from Return to Oz, TickTock the Clockwork Man’s brain runs down. Like AI systems, he needs human intervention to keep functioning safely. Without it, he hallucinates and spouts gibberish and unpredictable nonsense. As a small business owner or just a regular human trying to survive in this digital jungle, you might be wondering: “TechBear, how do I use these magical AI tools without shooting myself in the paw?” Excellent question, my dear reader! Let’s dive in. 7 AI Safety Tips That Won’t Make Your Eyes Glaze Over 1. Know What You’re Feeding the Machine AI systems learn from the data you provide. Think of them as digital toddlers with photographic memories—they remember EVERYTHING. Never upload sensitive customer information, financial records, or that embarrassing karaoke video from last year’s holiday party. Once it’s in there, consider it potentially exposed. 2. Check the Fine Print (Yes, Actually Read It) I know, I know—terms of service are about as exciting as watching paint dry. But some AI tools claim ownership of anything you create with them. Others might store your inputs for “training purposes.” Take five minutes to skim the privacy policy before uploading your business’s crown jewels. 3. Keep a Human in the Loop AI can make mistakes that are both hilarious and horrifying. That AI-generated email might sound professional until it promises your clients the moon, a pony, and delivery dates that violate the laws of physics. Always review AI-generated content before it goes public. 4. Use Strong Authentication “Password123” isn’t cutting it, Karen. Many AI tools contain valuable data and access. Use long passphrases, two-factor authentication, and consider a password manager. Your future self will thank you when you’re not explaining to clients why your account started sending crypto scams. 5. Be Skeptical of AI-Generated “Facts” AI systems can hallucinate faster than your cousin at Burning Man. They’ll confidently cite non-existent research, invent statistics, and reference products your company never made. Fact-check anything important, especially if it involves numbers, dates, or specific claims. 6. Limit Access and Permissions Not everyone on your team needs the admin keys to your AI kingdom. Set up proper access controls and only give people the permissions they actually need. Your summer intern probably doesn’t require access to generate company financial forecasts. 7. Keep Your AI Tools Updated Just like that smartphone collecting dust in your drawer, AI platforms receive security updates. Make sure you’re running the latest versions and applying patches promptly. Outdated software is basically hanging a “HACK ME” sign on your digital doorstep. The Ethical Minefield of AI Art and Content Now let’s wade into the murky waters of AI ethics. (Don’t worry, I brought ethical floaties!) AI art generators can create stunning visuals faster than you can say “starving artist.” But there’s a catch: these systems were trained on millions of images created by human artists who didn’t necessarily consent to having their work used this way. Similarly, AI writing tools learned from countless human-written articles, books, and posts. When you generate content with AI, are you participating in something problematic? The jury’s still out, but here are some best practices: Recommended External Resources: The Bottom Line AI tools are powerful allies for small businesses when used responsibly. They can help you compete with bigger companies, streamline workflows, and create content more efficiently. But like any tool, they come with risks that require attention. Remember: AI is meant to assist you, not replace your human judgment. Trust your instincts if something feels off, and don’t be afraid to pull the plug if necessary. That’s all for today’s Tech Tip Tuesday! This is TechBear, reminding you that in the tech forest, the prepared survive while the careless get their picnic baskets stolen. Stay safe out there, and see you next week! P.S. If you found these AI safety tips helpful, share them with a friend who still thinks “AI” stands for “Always Impressive” hair styling products. We all know someone. I’m TechBear, the resident IT Bear at Gymnarctos Studios, and your snarky, no-nonsense guide to navigating the digital wilderness. As the self-appointed “papa bear” of the digital world, I protect my technocubbies from the dangers lurking in the tech forest, including the AI wolves and cybersecurity bears that roam the tech forest. When I’m not wrestling rogue algorithms, you might find me optimizing network flow or judging your cable management. (Seriously, folks. It’s a mess!) P.S. Techbear used Claude.ai and ChatGPT to help generate the tips in this post.
7 Powerful Strategies to Avoid Digital Traps: April Fools’ Day Cybersecurity Tips

Welcome, my easily tricked cybercubs! 🐻 As your favorite ursine IT expert, I’m here with essential April Fools’ Day cybersecurity tips to keep you safe from the pranks, scams, and digital mischief running wild today. April 1st turns the internet into a playground for tricksters, but with the right precautions, you won’t be fooled. The Alarming Truth About April Fools’ Day Online But here’s the real kicker—did you know cybersecurity experts report a 23% increase in phishing attempts during the week surrounding April Fools’ Day? Scammers love taking advantage of lowered vigilance, disguising their attacks as harmless jokes. This isn’t just annoying—it can be downright devastating. That’s why knowing and following these April Fools’ Day cybersecurity tips is crucial to avoid falling for sneaky scams dressed up as pranks. Your Essential Digital Safety Toolkit: 7 Powerful Strategies 1. Master the Art of Link Investigation That email claiming you’ve won a luxury yacht? Unless you entered a millionaires-only raffle, it’s about as legitimate as claiming my grandfather is now a rug in a condo shared by Jeff Bezos and Tim Cook. Always scrutinize sender addresses and hover over links before clicking. The difference between amazon.com and amaz0n-special-offer.com could cost you dearly. 🔥 April Fools’ Day cybersecurity tips: Never trust links in unexpected emails. Double-check URLs before clicking! Helpful Resource: VirusTotal URL Scanner – Paste suspicious links here to check them against multiple security databases before clicking. 2. Establish Ironclad Verification Protocols Your CEO is highly unlikely to request gift cards via urgent email today (or any day). Many scammers use April Fools’ Day as an excuse to send fake emails pretending to be from a trusted source. When faced with unusual requests—especially those involving money or sensitive information—verify through a separate, trusted communication channel. 🔥 April Fools’ Day cybersecurity tips: If an email feels off, confirm its authenticity before taking action. Helpful Resource: FTC’s Guide to Recognizing Business Impersonation Scams 3. Embrace Healthy Download Skepticism That amazing “download now” button for unreleased software promising revolutionary features? It’s probably installing far more than you bargained for. Maintain strict discipline by sticking exclusively to official app stores and verified websites, even when the promises seem irresistible. 🔥 April Fools’ Day cybersecurity tip: Avoid “too good to be true” free downloads—scammers love baiting victims on April 1st! Helpful Resource: CISA’s Tips for Avoiding Malware 4. Recognize Fake Security Alerts When your device suddenly displays a “virus detected” pop-up with a conveniently placed fix-it button, recognize this as the digital equivalent of a wolf in sheep’s clothing. These deceptive tactics create false urgency designed to override your better judgment. 🔥 April Fools’ Day cybersecurity tips: Real security alerts don’t demand immediate action via pop-ups. Helpful Resource: How to Spot Tech Support Scams 5. Reject Unsolicited Tech Support Remember this golden rule: No legitimate tech company will ever call you out of the blue. Not today, not ever. These unsolicited calls are always scams designed to gain access to your devices or extract payment for non-existent problems. 🔥 April Fools’ Day cybersecurity tips: Hang up immediately if someone calls claiming to be “tech support.” Helpful Resource: Microsoft’s Guide to Avoiding Tech Support Scams 6. Deploy Multi-Factor Authentication Everywhere The most powerful protection against account compromise isn’t just a strong password—it’s adding that crucial second verification step. Enable MFA on every important account, especially financial services and email. 🔥 April Fools’ Day cybersecurity tips: MFA is like a double-lock for your accounts—activate it now! Helpful Resource: CISA’s Multi-Factor Authentication Guide 7. Cultivate Year-Round Digital Skepticism The best April Fools’ Day cybersecurity tip? Don’t let your guard down just because today is known for jokes. Cybercriminals exploit humor to mask their attacks. Stay skeptical, question urgency, and always verify before you act. 🔥 April Fools’ Day cybersecurity tips: Trust but verify—skepticism is your best defense year-round. Helpful Resource: National Cybersecurity Alliance’s Resources The Remarkable Benefits of Staying Vigilant By following these April Fools’ Day cybersecurity tips, you’ll be far less likely to fall victim to digital pranks, phishing scams, and security threats. Stay alert, stay skeptical, and most importantly—don’t get fooled! 💡 Bonus Fact: Users who implement these strategies experience 82% fewer security incidents than those who don’t. The small investment in awareness and caution pays extraordinary dividends in protected identities, secure finances, and digital peace of mind. Stay Smart, Stay Safe, Stay Skeptical Don’t become another statistic in the growing number of cybercrime victims. Embrace these April Fools’ Day cybersecurity tips today and transform yourself from potential target to informed defender. Remember: In the digital jungle, the alert bear avoids the trap while the distracted one steps right in. Stay sharp, stay skeptical, and stay safe, my dears! 🐻 About Tech Bear About TechBear: I’m TechBear, your go-to ursine IT guru, dispensing weekly tech tips and security advice so sweet, it’ll make your hard drive hum with delight. (And yes, I have a strict honey-pot-only payment policy. It’s an industry standard, didn’t you know?) I’ve battled rogue AI, debugged quantum entanglement, and once single-handedly restored the internet using only a paperclip and a rubber band. (Side effects of my advice may include increased productivity and a sudden urge to upgrade your RAM.) So, trust me on this. #TechTipTuesday #AprilFools #CyberSecurity #TechHumor #DigitalSafety #BearlyFooled #OnlineSafety
Two-Factor Authentication (2FA): Our Essential Tech Tip Tuesday Guide for Smartly Securing Your Accounts
Passwords Aren’t Enough! Why You Need Two-Factor Authentication (2FA) Right Now Alright, listen up, my fabulous tech cubs. What the heck is two-factor authentication (2FA)? I’m glad you asked. If you’re still walking around the internet with just a password protecting your accounts, honey, you might as well be leaving your front door wide open with a neon sign that says, “Come on in, hackers!” 🚨 Passwords alone aren’t enough anymore. Cybercriminals have all sorts of sneaky tricks—phishing emails, credential stuffing, brute force attacks—to get into your accounts. And let’s be real: if your password is something like password123 or Fluffy1997, sweetie, you’re basically handing them the keys. That’s where 2FA swoops in like a fabulous, high-tech security blanket. What Is Two-Factor Authentication? Two-factor authentication (2FA) is a simple yet powerful security measure that requires two different forms of verification to log into an account. Instead of just entering a password, you also need a second factor, like a one-time code or a biometric scan. Think of it like this: If your password is the lock on your front door, then 2FA is the deadbolt, security camera, and guard dog all in one. 🐻🔒 Types of Two-Factor Authentication Not all 2FA methods are created equal. Choosing the right two-factor authentication (2FA) method depends on your needs, tech comfort level, and security priorities. Let’s break it down in plain English, so you can pick the best option for you and your business. 1️⃣ SMS Codes (Text Message Authentication) How it works: When you log in, a code is sent to your phone via text. You enter the code to confirm your identity. ✅ Pros:✔️ Super easy to set up—just link your phone number.✔️ No need to install extra apps or buy anything.✔️ Better than relying on just a password. ❌ Cons:🚨 Hackable via SIM-swapping attacks—hackers can trick your phone carrier into transferring your number to their device.📶 Requires a cell signal, so it won’t work in areas with poor reception.📱 Tied to your phone number, so if you lose your phone or change numbers, you might get locked out. 👨💼 Best for: Home users who need a basic security boost but don’t want to deal with apps. 2️⃣ Authenticator Apps (The Recommended Option!) How it works: You install an app like Google Authenticator, Microsoft Authenticator, or Authy. It generates a time-sensitive, one-time-use code when you log in. ✅ Pros:✔️ Much more secure than SMS—codes are generated locally on your phone, not sent over the internet.✔️ No risk of SIM-swapping attacks since it doesn’t rely on your phone number.✔️ Works even without a cell signal (as long as your phone is on).✔️ Free to use and widely supported. ❌ Cons:📲 You must have your phone with you to log in.🔑 If you lose your phone, you need backup codes or a recovery method (which many people forget to set up).📌 Not as easy to set up as SMS, but still pretty user-friendly. 👨💼 Best for: Small businesses, home users, and anyone looking for a strong, reliable security option without extra costs. 🔹 Pro Tip: If you use an authenticator app, store your backup codes somewhere safe! If you lose access to your phone, these codes will save you. 3️⃣ Hardware Security Keys (The Gold Standard for Security) How it works: You plug in a USB key (like YubiKey or Google Titan) or tap a wireless NFC key to verify your identity. ✅ Pros:✔️ Virtually unhackable—no phishing, no SIM-swapping, no password leaks.✔️ No need to remember or type codes—just plug in the key and go.✔️ Works offline and doesn’t require a phone.✔️ Great for business security, especially for employees handling sensitive data. ❌ Cons:💰 Costs money—usually between $20–$60 per key, depending on the brand and features.🔑 You must keep track of the physical key—lose it, and you’ll need a backup.📌 Not as widely supported as other methods (though adoption is growing). 👨💼 Best for: Small businesses, IT professionals, and high-risk users (like financial managers, journalists, and executives). 🔹 Pro Tip: If you go this route, buy two security keys—one as a backup in case you lose the main one. 4️⃣ Biometric Authentication (Your Face or Fingerprint) How it works: You log in using Face ID, fingerprint scanners, or retina scans—no passwords or codes required. ✅ Pros:✔️ Super convenient—just scan your face or finger.✔️ Fastest way to log in.✔️ Hard to steal—hackers can’t “guess” your fingerprint. ❌ Cons:🤷 Not all websites support biometric login yet.🔄 You might need a backup method (like an authenticator app or password).📌 Could be bypassed with a stolen or cloned fingerprint (though rare). 👨💼 Best for: Home users and small businesses already using smartphones with biometric security. 🔹 Pro Tip: Use biometrics alongside another 2FA method, not as your only protection. Which 2FA Method Should You Use? 2FA Type Security Level Ease of Use Best For SMS Codes ⭐⭐☆☆☆ (OK) ⭐⭐⭐⭐☆ (Easy) Home users, beginners Authenticator App ⭐⭐⭐⭐☆ (Good) ⭐⭐⭐☆☆ (Moderate) Small businesses, tech-savvy users Security Keys ⭐⭐⭐⭐⭐ (Best) ⭐⭐☆☆☆ (Harder) High-risk users, businesses Biometrics ⭐⭐⭐⭐☆ (Good) ⭐⭐⭐⭐⭐ (Easiest) Smartphone users, convenience seekers Which One is Right for You? 🔹 If you’re not super techy, start with SMS-based 2FA—it’s better than nothing!🔹 If you want strong security, use an authenticator app like Google Authenticator.🔹 If you run a small business, consider security keys for ultimate protection.🔹 If you love convenience, enable biometric authentication where possible. 💡 Best Practice: Use multiple 2FA methods whenever possible. For example, use an authenticator app as your primary method and keep a security key or backup codes in case you lose your phone. Why You Need 2FA (Like, Yesterday) Still not convinced? Here’s why enabling two-factor authentication is non-negotiable: 🚫 Stops Password Leaks in Their TracksEven if a hacker steals your password, they still need the second factor to get in. 🛡️ Protects Against Phishing & Credential TheftPhishing emails are getting sneaky, but without your second factor, hackers hit a dead end. 💰 Safeguards Your Finances & IdentityBank accounts, cryptocurrency wallets, PayPal—without 2FA,
